spfXio.com makes it easy for you to implement an effective DMARC using our management platform. While we may make it easy, we encourage anyone responsible for domain email security to develop a foundational knowledge of DMARC, its purpose, how it is implemented, and how it is verified.
What is Domain-based Message Authentication, Reporting, and Conformance (DMARC)?
DMARC is a protocol defined by the Internet Engineering Task Force (IETF) that provides facilities for email receivers to authenticate email and email senders to both publish authentication policies and collect feedback regarding authentication performance. DMARC authentication functions largely on top of underlying SPF and DKIM protocols, requiring at-lest one of the protocols to authenticate in a DMARC aligned way. This means that if SPF passes, the SMTP Envelope from domain must match the DMARC domain or, similarly, a valid DKIM signature from the sending domain must be verified. Once the DMARC authentication state is determined, receiving infrastructure may request policies to be followed to disposition DMARC failed messages. This dispositioning may include no-action, quarantining DMARC failed emails, or outwardly rejecting emails. In all cases, receivers may elect to provide feedback periodically in the form of aggregated authentication results or forensic reports. For a full technical understanding, it is best to read, re-read, and then read again the IETF document found at https://datatracker.ietf.org/doc/html/rfc7489.
The following diagram provides a walk-through and logical evaluation of DMARC authentication.
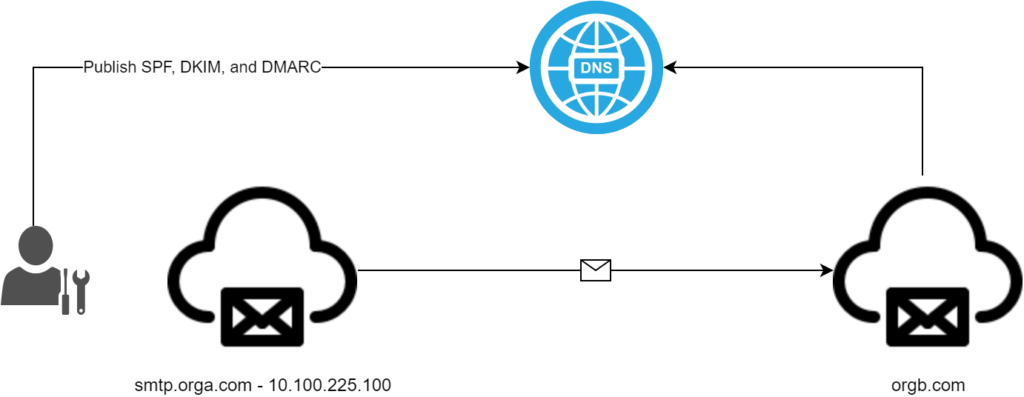
DMARC Evaluation during an SMTP Conversation
- orga.com sends an email to orgb.com through smtp.orga.com server with IP Address 10.100.225.100 and applies a digital signature using the private key of orga.com
- orb.com receives the email and performs a TXT record lookup for orga.com in an attempt to identify an SPF Record; the following record is returned:v=spf1 mx include:spf.orga.com ip4:10.100.225.100\32 ptr:smtp.orga.com -all
- Identified SPF records are evaluated to confirm if the sending IP Address is authorized to send on behalf of orga.com.
- If the sending system is authorized by the domain’s SPF record, SPF authentication results in a pass.
- orb.com receives also extracts the DKIM signature, and performs a TXT record lookup for a public domain key published at orga.com.
- The received public key is used to verify the DKIM signature extracted from the received email headers.
- If the signature is verified, DKIM authentication provides a pass result.
- After SPF and DKIM authentication cycles are complete, DMARC policies are requested from orga.com. If a valid policy is returned, DMARC authentication is initiated.
- If either SPF or DKIM pass in alignment with orga.com, DMARC authentication results in a pass result or otherwise results in a fail.
- If a received email fails DMARC authentication, the action of orga.com’s published DMARC record is evaluated during dispositioning.
- DMARC records may instruct receivers to take no action, quarantine, or reject emails failing DMARC authentication.
- DMARC results are aggregated and sent to destinations published in orga.com’s DMARC record.
